Public and Private-key cryptography
Public-key cryptography is the backbone of most distributed systems. It provides both a way to encrypt a message and to confirm the source of a message, without the need to agree upon a shared key. It is used in a wide variety of protocols and data formats, which are implemented by a huge range of application and system software.
Private-key cryptography send encrypted messages across a network. So that if anyone was to get their hands on the message, they wouldn’t be able to read it unless they could decode the encryption.
I want to send you a message and don’t want anyone else to read it but you. I encrypt the message using a private key and only you and I have this private key. We would then use the key to encrypt and decrypt the same message. This is called a symmetric cryptography.
- SSL (https) protocol
- SSH (secure remote login, tunneling, etc)
- Digitally signed PDF files (including attachments within the PDF)
- Signed Applets and jar archive files for Java
- Digital signatures in the packaging infrastructure for Debian, Ubuntu and RedHat Linux distributions, etc.
- PGP/GPG for signed and/or encrypted files and email .
- S/MIME for signed and/or encrypted email
- DNSSEC for securing the DNS
- Internet Key Exchange (IKE) in IPsec for secure low-level TCP/UDP networking
- RFC 3161 for authenticated timestamps
- A variety of other uses, like digital cash and secure transparent voting .
If two parties wanted to safely exchanges messages before public key cryptography, they had to agree on a common code. This code is referred to as a cipher. One of the more famous of such encryption systems is the Ceasar cipher. With a Ceasar cipher, every character of the message is offset by an agreed upon number. Yet, if a third party manages to intercept the transmission of the cipher itself, all encrypted messages can be decoded. Thus, a trusted third party network is required to safely exchange the cipher.
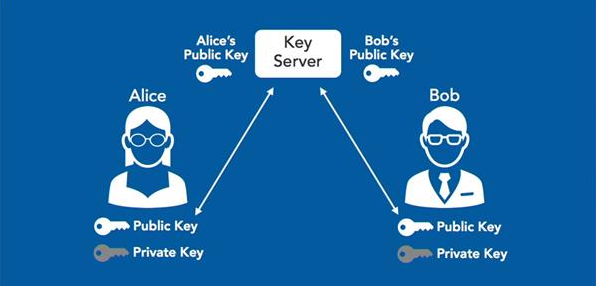
Public key cryptography uses a pair of hashes instead. These hashes are often referred to as the keys. The keys are algorithmically generated so that they are cryptographically connected. This means that a message encrypted with one key can only be decrypted with the other key and vice versa.
One of these keys can be broadcasted. As a result, everyone knows that this key is connected to the owner’s identity. Therefore, it is referred to as the public key. The other key will be held privately. It is very important that nobody except the owner knows the content of this key, as it will be used to prove the owner’s identity. It is therefore referred to as the private key.
Because no cipher has to be exchanged, there is no need for the trusted middleman to exchange the cipher. This eliminates a key weakness of cipher encryption.
The Caesar cipher, also known as a shift cipher, is one of the simplest forms of encryption. It is a substitution cipher where each letter in the original message (called the plaintext) is replaced with a letter corresponding to a certain number of letters up or down in the alphabet.